Latest posts
 In recent years, the global community has shown remarkable flexibility in the face of new challenges. Previous technology has become obsolete at a rapid rate because of this. Websites, programs, and the Blockchain are ju
In recent years, the global community has shown remarkable flexibility in the face of new challenges. Previous technology has become obsolete at a rapid rate because of this. Websites, programs, and the Blockchain are ju
.png) Pinterest.com allows users to explore, save, and share images and videos found on virtual boards. Pinterest has a significant number of users who, over 400 million active users, use it as a resource to find inspiration a
Pinterest.com allows users to explore, save, and share images and videos found on virtual boards. Pinterest has a significant number of users who, over 400 million active users, use it as a resource to find inspiration a
 It's been said that a picture is worth a thousand words, but the ideal photograph is worth far more than that. It is more essential than ever to ensure that the photographs you take are of the highest quality possibl
It's been said that a picture is worth a thousand words, but the ideal photograph is worth far more than that. It is more essential than ever to ensure that the photographs you take are of the highest quality possibl
Digital Marketing
 Google Publisher Subscription is a great way to get more clicks and impressions from your Google search results. It&rsqu
Google Publisher Subscription is a great way to get more clicks and impressions from your Google search results. It&rsqu Search Engine Optimization (SEO) is a constantly changing and ever-evolving strategy. In fact, many experts estimate
Search Engine Optimization (SEO) is a constantly changing and ever-evolving strategy. In fact, many experts estimate A company that specializes in web design is known as a web design agency. Web design agencies offer a variety of service
A company that specializes in web design is known as a web design agency. Web design agencies offer a variety of service Because of its ability to reduce wasted time and boost overall output, technology has emerged as an indispensable instru
Because of its ability to reduce wasted time and boost overall output, technology has emerged as an indispensable instru Every day, it seems, news emerges of yet another corporation whose existence has been shattered by a data leak or anothe
Every day, it seems, news emerges of yet another corporation whose existence has been shattered by a data leak or anothe
WordPress
- Google Publisher Subscription is a great way to get more clicks and impressions from your Google search results. It’s an easy way to increase traffic, better reach your target market, and improve your SEO by Incrementors. In this guide, we’ll outline th
- Hosting in the Cloud That Is Ideal for WordPress Websites You are need to have a web presence before you can begin developing your blog. You must have a website and the capacity to broadcast videos in real time in order to attract readers as well as potential sp
- As a web designer or developer, you should already be aware that WordPress and websites go hand in hand today. WordPress terminology is often misunderstood, with themes and templates sometimes being conflated. This is not the case. We'll go over all you n
- For enterprises, advertisers, and bloggers, having a list of approved WordPress hosting providers is a great help. Google gives advice on where to host a blog, where to host a website, and where to host a personal website. WordPress and other platforms may be ho
Gallery
Inspiration
 Every day, it seems, news emerges of yet another corporation whose existence has been shattered by a data leak or another piece of software that has caused enormous chaos. Businesses need excellent software development t
Every day, it seems, news emerges of yet another corporation whose existence has been shattered by a data leak or another piece of software that has caused enormous chaos. Businesses need excellent software development t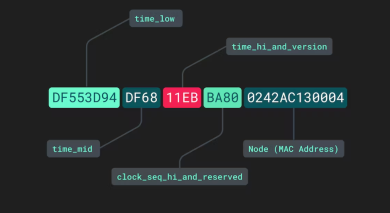 The id column is the primary method of record identification in any database. Most databases are set up to automatically produce a numeric id, often beginning with 1 and increasing by 1 with each new record. However, a UUID is not the only choice for id fields (universally unique identifie
The id column is the primary method of record identification in any database. Most databases are set up to automatically produce a numeric id, often beginning with 1 and increasing by 1 with each new record. However, a UUID is not the only choice for id fields (universally unique identifie To be honest, as a digital marketer, you probably have no idea how much of an advantage learning Adobe Illustrator could be for you... And why would you, if your web presence is excellent, your branding materials are top-notch, and your return on investment is solid? What if you, however,
To be honest, as a digital marketer, you probably have no idea how much of an advantage learning Adobe Illustrator could be for you... And why would you, if your web presence is excellent, your branding materials are top-notch, and your return on investment is solid? What if you, however, Illustrator CC 2022 concludes our series on the latest additions to Adobe's Creative Suite. Here you may learn everything you need to know about Adobe InDesign and Photoshop. PREPARING THE WAY FOR ILLUSTRATOR CC 2022 It's hardly a big surprise that the newest version of Illustr
Illustrator CC 2022 concludes our series on the latest additions to Adobe's Creative Suite. Here you may learn everything you need to know about Adobe InDesign and Photoshop. PREPARING THE WAY FOR ILLUSTRATOR CC 2022 It's hardly a big surprise that the newest version of Illustr An Adobe After Effects lower thirds overlay is a necessity for any video editor. It's common for these overlays to take up the whole bottom third of a video, serving as further information. Below are three of the most common applications of lower thirds in the world of video product
An Adobe After Effects lower thirds overlay is a necessity for any video editor. It's common for these overlays to take up the whole bottom third of a video, serving as further information. Below are three of the most common applications of lower thirds in the world of video product
FEATURED POSTS
 Google Publisher Subscription is a great way to get more clicks and impressions from your Google search results. It’s an easy way to increase traffic, better reach your target market, and improve your SEO by Increm
Google Publisher Subscription is a great way to get more clicks and impressions from your Google search results. It’s an easy way to increase traffic, better reach your target market, and improve your SEO by Increm Hosting in the Cloud That Is Ideal for WordPress Websites You are need to have a web presence before you can begin developing your blog. You must have a website and the capacity to broadcast videos in real time in order to attract readers as well as potential sponsors. A platform that a
Hosting in the Cloud That Is Ideal for WordPress Websites You are need to have a web presence before you can begin developing your blog. You must have a website and the capacity to broadcast videos in real time in order to attract readers as well as potential sponsors. A platform that a As a web designer or developer, you should already be aware that WordPress and websites go hand in hand today. WordPress terminology is often misunderstood, with themes and templates sometimes being conflated. This is not the case. We'll go over all you need to know about WordPre
As a web designer or developer, you should already be aware that WordPress and websites go hand in hand today. WordPress terminology is often misunderstood, with themes and templates sometimes being conflated. This is not the case. We'll go over all you need to know about WordPre For enterprises, advertisers, and bloggers, having a list of approved WordPress hosting providers is a great help. Google gives advice on where to host a blog, where to host a website, and where to host a personal website. WordPress and other platforms may be hosted by many of the compa
For enterprises, advertisers, and bloggers, having a list of approved WordPress hosting providers is a great help. Google gives advice on where to host a blog, where to host a website, and where to host a personal website. WordPress and other platforms may be hosted by many of the compa
Digital Marketing
 Google Publisher Subscription is a great way to get more clicks and impressions from your Google search results. It’s an easy way to increase traffic, better reach your target market, and improve your SEO by Increm
Google Publisher Subscription is a great way to get more clicks and impressions from your Google search results. It’s an easy way to increase traffic, better reach your target market, and improve your SEO by Increm Search Engine Optimization (SEO) is a constantly changing and ever-evolving strategy. In fact, many experts estimate that Google updates its search algorithm around 500-600 times a year—once or twice each day. While most of these changes don't majorly impact your website'
Search Engine Optimization (SEO) is a constantly changing and ever-evolving strategy. In fact, many experts estimate that Google updates its search algorithm around 500-600 times a year—once or twice each day. While most of these changes don't majorly impact your website' A company that specializes in web design is known as a web design agency. Web design agencies offer a variety of services to their clients, including the creation, development, and maintenance of websites. The majority of these organizations have at their disposal a group of professionals
A company that specializes in web design is known as a web design agency. Web design agencies offer a variety of services to their clients, including the creation, development, and maintenance of websites. The majority of these organizations have at their disposal a group of professionals Because of its ability to reduce wasted time and boost overall output, technology has emerged as an indispensable instrument in the expansion of businesses. In today's business world, practically every firm needs to have their own in-house technology team as well as an outside perspect
Because of its ability to reduce wasted time and boost overall output, technology has emerged as an indispensable instrument in the expansion of businesses. In today's business world, practically every firm needs to have their own in-house technology team as well as an outside perspect Every day, it seems, news emerges of yet another corporation whose existence has been shattered by a data leak or another piece of software that has caused enormous chaos. Businesses need excellent software development teams if they want to keep up with the competition in today's incre
Every day, it seems, news emerges of yet another corporation whose existence has been shattered by a data leak or another piece of software that has caused enormous chaos. Businesses need excellent software development teams if they want to keep up with the competition in today's incre